Project policies
Project policies let you control permissions per project and per role in a granular way. Policies define rules for project entities and centralize how access is managed for a role in a specific project. Each project policy consists of a set of granted and denied permissions, giving you precise control over what actions users can and cannot perform.
Unlike Default permissions, project policies can target specific entities that are part of a project such as specific compositions, patterns, component definitions, or content types.
Permission groups and actions#
The following groups can be targeted in a project policy, with the listed actions:
Assembly permissions#
- Compositions:
Read draft,Read published,Create,Update,Delete,Publish- Can be targeted by the following criteria:
- By composition type
- By composition pattern
- Specific compositions
- Can be targeted by the following criteria:
- Composition patterns:
Read draft,Read published,Create,Update,Delete,Publish- Can be targeted by the following criteria:
- By component type
- Specific composition patterns
- Can be targeted by the following criteria:
- Component patterns:
Read draft,Read published,Create,Update,Delete,Publish- Can be targeted by the following criteria:
- By component type
- Specific component patterns
- Can be targeted by the following criteria:
- Project map:
Manage - Redirects:
Read,Create,Update,Delete - Releases:
Read,Create,Update,Delete,Launch - AI prompts:
Read,Manage
Content permissions#
- Entries:
Read draft,Read published,Create,Update,Delete,Publish- Can be targeted by the following criteria:
- By content type
- By entry pattern
- Specific entries
- Can be targeted by the following criteria:
- Entry patterns:
Read draft,Read published,Create,Update,Delete,Publish- Can be targeted by the following criteria:
- By content type
- Specific entry pattern
- Can be targeted by the following criteria:
- Assets:
Read,Create,Update,Delete
Model permissions#
- Components:
Read,Manage - Content types:
Read,Manage - Data sources:
Read,Manage - Data types:
Read,Manage
Optimization permissions#
- Manifest:
Read draft,Read published,Publish - Signals:
Read,Create,Update,Delete - Intents & audiences:
Read,Create,Update,Delete - Enrichments:
Read,Create,Update,Delete - Quirks:
Read,Create,Update,Delete - Tests:
Read,Create,Update,Delete
How policies are evaluated#
- Policies are assigned per role, per project.
- If a project policy exists for a role, it determines that role's permissions in the project.
- If no project policy exists, the role's default permissions apply.
- If a user has multiple roles in a project, their permissions are combined. See how permissions are evaluated for details on how permissions are resolved across multiple roles.
Create and manage project policies#
Add a project policy#
- In Uniform, navigate to Security > Roles in your team dashboard.
- Click the name of the role you want to configure.
- In the Project policies section, click Add project.
- Select the project you want to create a policy for.
- Configure the permissions in the policy panel (see Configure permissions below).
- Click Ok to save the project policy.
- Click Save to save the role.
Copy project policies to other projects
You can copy project policies to other projects within the Uniform roles editor. This feature is useful if you want to keep similar projects in sync, such as different environments like development, staging, and production. Copying project policies is also helpful for promoting permission changes from a lower environment to a production project.
To copy a project policy select the menu on the project policy and select Copy to project.
Configure permissions#
When editing a project policy, you configure permissions in the Granted and Denied sections. Permissions that are added to the Granted section are allowed for the role in that project.
Understanding denied permissions
Any permission not explicitly granted is denied by default. Use the Denied section to explicitly remove previously granted permissions (for example, removing some specific content types or entries). The denied permission may have be granted by the same role or a different role.
Using the permissions editor:
- Filter by permission group: Use the dropdown to filter permissions by permission group (Assembly, Content, Modeling, Optimization). This helps you focus on related permissions when configuring complex roles.
- Reorder by type: Click Reorder by type to group related permissions together for a better overview.
- Apply preset: Use the Apply preset dropdown to quickly apply a predefined set of permissions (Developer, Editor, or Viewer).
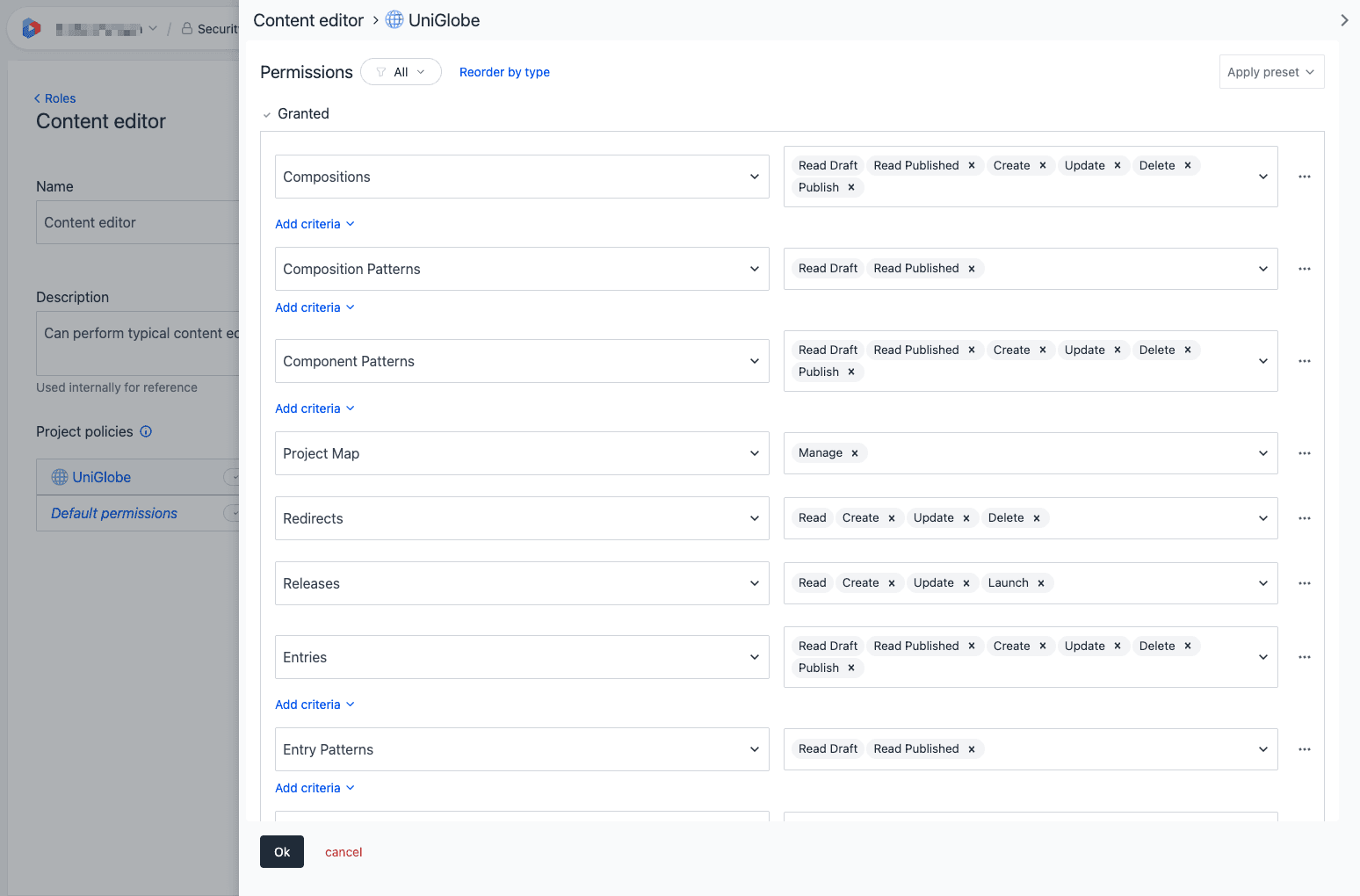
Target specific entities#
For Compositions, Entries, and Patterns, you can target specific entities instead of granting broad permissions:
- Find the entity type (e.g., Compositions, Entries) in the permissions list.
- Click Add criteria below the entity.
- Select how you want to target:
- By type: Target all entities of a specific composition type, content type, or component type.
- By pattern: Target entities that match a specific composition pattern, component pattern, or entry pattern.
- Specific entities: Target individual compositions, entries, or patterns by selecting them directly.
- Configure the actions you want to allow for the targeted entities.
This allows you to create rules like "Allow editing only Blog Post entries" or "Allow publishing only Marketing Page compositions."
Common scenarios#
For step-by-step examples of how to configure project policies for specific use cases, see the common scenarios guide.
Common scenarios for configuring project policies
Step-by-step examples for common permission configurations.
Related guides#
Project policy CLI commands
Manage policy documents via the CLI to push, pull, and sync permissions across projects.
API keys
Create and manage API keys to interact with Uniform.
Users
Manage user accounts within the Uniform platform.